President Candy Yoder opened the meeting and introduced Shannon White who informed the club about the passing of long time club member Phil Penn on August 29. Shan shared thoughtful words, led the Pledge, and Four-Way Test.
Guests were introduced by Paul Warning, including Chris Frey (Susan Bossung), Erin McNeal (Ashley Bowen), and Dave Miller (Paul Warning). Welcome to ALL, we hope you can all join us again some other time!
Announcements for September 9:
- Candy announced the upcoming 2019 Rotary Zones 30-31 All Club Luncheon scheduled for Friday, October 11 at the 2019 Rotary Summit in Fort Wayne. Elkhart Rotary Club has been asked to present its Wellfield Botanic Gardens project as a way of 'thinking big' about community projects. Eric Garton and Eric Amt will be coordinating the presentation.
- Julie Cotton announced that RSVPs are being taken for our Monday, September 30 - - the FIFTH MONDAY - - Rotary Dinner at Matterhorn, a special event in lieu of our regular Monday luncheon. Drinks and happy hour begin at 5:30 p.m. Musical entertainment provided generously by Steve Gruber, featuring songs of remembrance from our past. RSVP to Julie Cotton, along with your song requests and photos from the past for a special slideshow. Cost is $25 per person.
- Julie also announced that there are still TWO TICKETS LEFT to the October 4 Dionne Warwick concert at the Lerner; if you're interested, contact Julie directly. Billing will be done through your account.
- Eric Garton thanked club members, whether actively volunteering at Taste of the Gardens, helping with its coordination, sponsoring, or simply helping spread the word about this great event. In total, nearly 3500 attended Taste of the Gardens on Sunday; more financial reporting to follow. It was a fantastic event and your help is appreciated!!
- Doug Risser announced the upcoming friendship exchange that will take place March 1-14, 2020 to Sao Paolo, Brazil. For more information contact Doug directly.
.jpg)
- Phishing: In some respects, phishing is a confidence trick, designed by would-be thieves in order to part unsuspecting computer users from their most precious personal and/or financial information. Traditionally, phishing attempts looked to acquire data such as bank account details, social security numbers, and credit card numbers, either for direct financial gain or to facilitate identity theft (more on that below). Over the last few years, however, other forms of data and information have become valuable too. Phishing attempts are now just as likely to target users of social networking sites in order to try and steal their accounts either to use them as a launchpad for socially engineered scams or as a means of spamming the victim’s friends and other contacts. Phishing scams usually arrive via email and are designed to appear to be from legitimate organisations so as to trick the recipient into responding with their personal information. Many will even spoof email headers so that they appear to have come from a trusted source, or link to fake websites that are clones of the official sites that they purport to be. An example pictured below, creates the issue of 'urgency' to get the user to fall for the scheme.
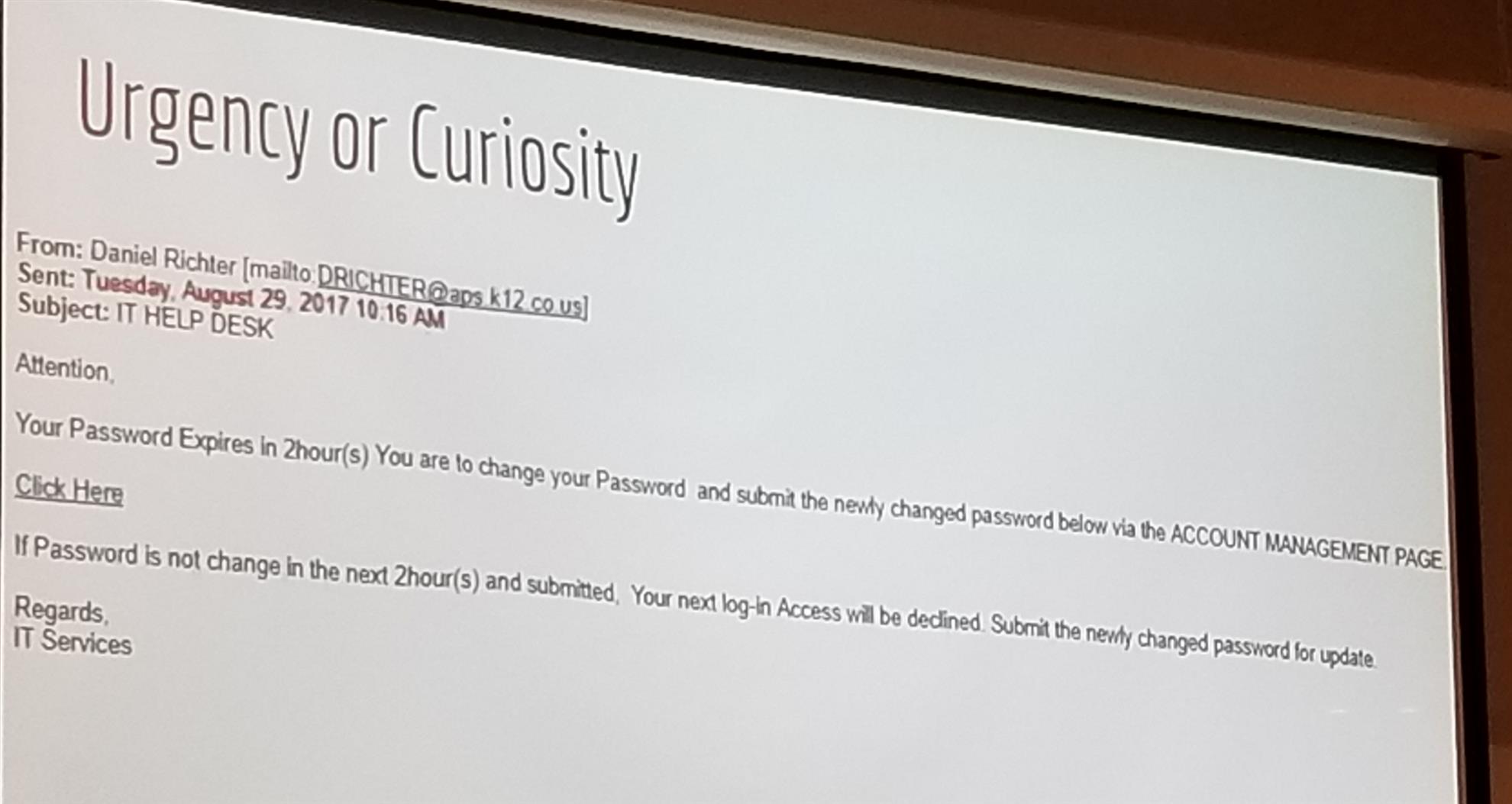
- Generic Greetings
- Password Attacks - - there are three types:
- Brute Force Attack - - A hacker uses a computer program or script to try to log in with possible password combinations, usually starting with the easiest-to-guess passwords. (So just think: if a hacker has a company list, he or she can easily guess usernames. If even one of the users has a “Password123”, he will quickly be able to get in.)
- Dictionary Attack - - A hacker uses a program or script to try to login by cycling through combinations of common words.
- Key Logger Attack - - A hacker uses a program to track all of a user’s keystrokes. So at the end of the day, everything the user has typed—including their login IDs and passwords—have been recorded. A key logger attack is different than a brute force or dictionary attack in many ways. Not the least of which, the key logging program used is malware (or a full-blown virus) that must first make it onto the user’s device (often the user is tricked into downloading it by clicking on a link in an email). Key logger attacks are also different because stronger passwords don’t provide much protection against them, which is one reason that multi-factor authentication (MFA) is becoming a must-have for all businesses and organizations.
- HOW TO AVOID Password Attacks: Use two-factor authentication (also called multi-factor authentication, 2FA, and advanced authentication), a user is required to not only provide a password to gain access to the system, but also a another security “factor,” like a unique one-time access code generated from a token device or secure mobile app on their smartphone.
- You SHOULD USE a 'Password Manager' application such as Dashlane to help you in keeping track of myriad passwords; they're handy and secure.
- Eavesdropping: an electronic attack where digital communications are intercepted by an individual whom they are not intended.
This is done in two main ways: Directly listening to digital or analog voice communication or the interception or sniffing of data relating to any form of communication. Be cautious what wifi networks you're using, especially in public spaces... can you trust the wifi you're connected to.
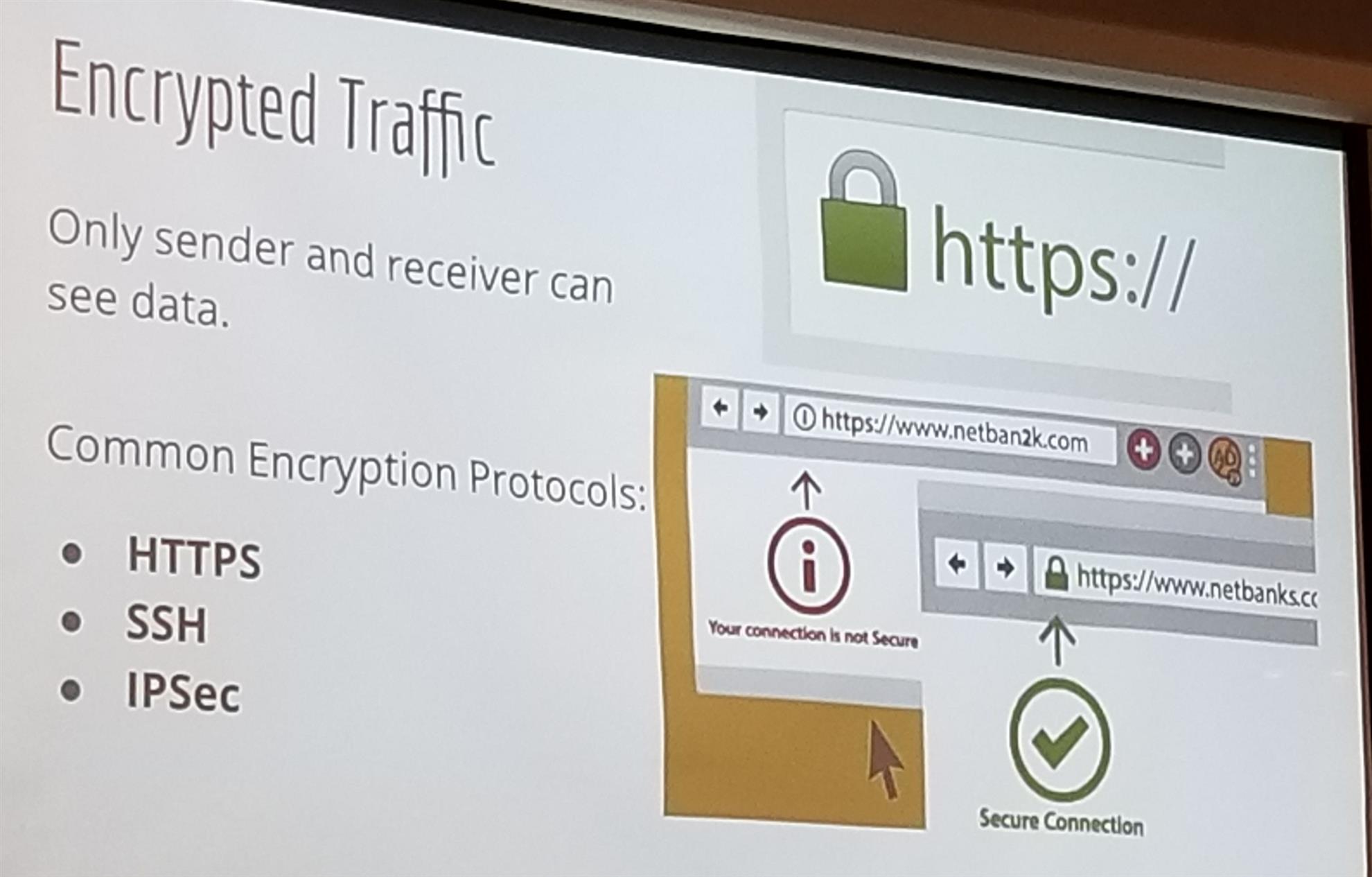
Encrypted Traffic: To ensure safe web use, be sure you're working in spaces that have their information encrypted for security. And Jason reminded everyone, when in doubt, just delete it! IF it's an actual email, you'll receive another email. Better to be safe than sorry
- Malware and Ransonware: Ransomware is a type of malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid. Ransomware typically spreads through phishing emails or by unknowingly visiting an infected website. Ransomware can be devastating to an individual or an organization.
- Cryptojacking: .... whoa, let's take a step back a bit... first, what ARE cryptocurrencies? Two words—“cryptography” and “currency”—combine to form “cryptocurrency." Cryptocurrencies are forms of digital money that exist only in the online world, with no actual physical form. All cryptocurrencies exist as encrypted decentralized monetary units, freely transferable between network participants. Or put more simply, cryptocurrency is electricity converted into lines of code, which have a real monetary value.They were created as an alternative to traditional money, and gained popularity for their forward-looking design, growth potential, and anonymity. One of the earliest, most successful forms of cryptocurrency, Bitcoin, came out in 2009. By December 2017, the value of a single bitcoin had reached an all-time high of nearly $20,000 USD, then dropped below $10,000. Bitcoin’s success inspired dozens of other cryptocurrencies that operate in more or less the same way. Less than a decade after its invention, people all over the world use cryptocurrencies to buy things, sell things, and make investments.So back to cryptojacking....
Cryptojacking (also called malicious cryptomining) is an emerging online threat that hides on a computer or mobile device and uses the machine’s resources to “mine” forms of online money known as cryptocurrencies. It’s a burgeoning menace that can take over web browsers, as well as compromise all kinds of devices, from desktops and laptops, to smart phones and even network servers. Like most other malicious attacks on the computing public, the motive is profit, but unlike many threats, it’s designed to stay completely hidden from the user.
To view the student and faculty portal for the Office of Information Technology, visit their website https://infosec.nd.edu/. This gives you an idea of the level of security and protection Jason and his team attempt to offer the students and faculty of Notre Dame. Surf safe out there!
- September 16: Richard Pfeil, Co-founder of the Pfeil Innovation Center
- September 23: Gregg Fore, C&G Media Group, The State of the RV Industry
- September 30: Rotary Dinner at Matterhorn, **A special fifth Monday dinner event**, RSVP to Julie Cotton, $25 billable to your account


